Supply Chain Risks in the Software Development Life Cycle

In the aftermath of the Heartbleed vulnerability, the software industry began to understand that neglecting to rigorously test third-party libraries was a fatal oversight. OpenSSL, an open-source software extensively used for secure communications, contained a bug that allowed unauthorized access to sensitive information. Even though OpenSSL wasn’t developed by the organizations that suffered due to Heartbleed, they had to bear the brunt as they had incorporated this vulnerable third-party library into their systems.
The Heartbleed incident reinforced the importance of robust SSDLC principles, an approach that integrates security practices directly into the software development life cycle. Key components of SSDLC include requirements analysis, design, coding, testing, and maintenance, all with a focus on security from the outset. In particular, the “shift-left” approach emphasizes the need to consider security issues as early as possible in the life cycle, rather than retrospectively applying patches and fixes to developed software.
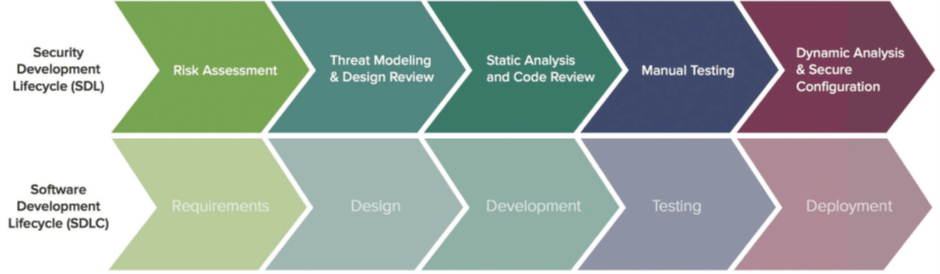
Static and Dynamic Code Analysis
Static and dynamic code analyses serve as invaluable tools in an SSDLC approach. Static code analysis involves analyzing the source code without executing the program, allowing for the detection of vulnerabilities in the early stages. On the other hand, dynamic code analysis involves examining the software while it is running, enabling the identification of runtime errors that static analysis might miss. Combining these approaches provides a comprehensive view of potential vulnerabilities in both the developed code and third-party libraries.
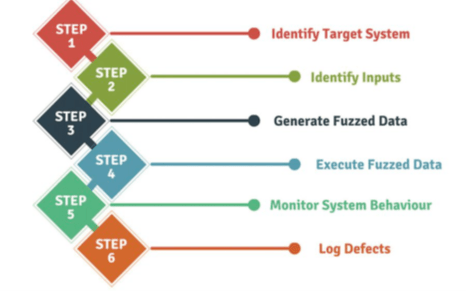
Fuzzing, also known as fuzz testing, is a highly effective technique employed during static code analysis. At its core, fuzzing involves injecting deliberately malformed or unexpected data into a software system in order to uncover vulnerabilities like crashes, memory leaks, or unexpected behaviors. By feeding a system with a broad range of irregular inputs, developers can identify issues that might go unnoticed during regular testing but could be potentially exploited in real-world scenarios.
One significant advantage of fuzzing lies in its ability to automate the discovery of new, previously unknown vulnerabilities. Conventional static analysis tools rely heavily on detecting known patterns of insecure code. While such tools are effective for catching common and well-understood issues, they may not discover novel or complex vulnerabilities. Fuzz testing, on the other hand, does not rely on known vulnerability patterns, but rather on the system’s behavior when confronted with irregular inputs. This makes fuzzing a powerful tool for unearthing previously uncharted vulnerabilities.
That said, effectively implementing fuzzing in static code analysis requires careful planning and execution. For starters, developers need to decide on the types of inputs to use for testing. These could range from totally random data to inputs that are slightly modified versions of normal ones. The latter, often known as “mutational fuzzing,” can be particularly useful for discovering edge-case issues. Also, interpreting fuzzing results can be complex, as not all irregular behaviors indicate a security vulnerability. Therefore, it’s vital to incorporate fuzz testing as a part of a comprehensive SSDLC, alongside other static and dynamic analysis techniques, for a well-rounded understanding of a software system’s security posture.
Security evaluators at Deutsche Telekom recently discovered a vulnerability in MatrixSSL library using code coverage-guided fuzzers (AFL and libFuzzer), and AddressSanitizer, a tool for detecting memory errors. CVE-2022-43974 is a buffer overflow vulnerability that could allow information disclosure and remote code execution. The software library has been patched.
MatrixSSL is an open-source, embedded Secure Sockets Layer (SSL) and Transport Layer Security (TLS) library. It is an open-source version of Rambus TLS toolkit . MatrixSSL is written in C and provides a minimalistic, high-performance option for adding SSL/TLS functionality to embedded or resource-constrained applications, devices, and systems.

One of the most significant advantages of MatrixSSL is its small memory footprint. The lightweight nature of the library makes it a popular choice for use in IoT devices, real-time systems, and other environments where system resources are at a premium.
MatrixSSL supports a range of cryptographic algorithms and is compliant with key industry standards. This makes it flexible and adaptable to different security requirements and regulatory environments. MatrixSSL also includes functionality to parse and validate X.509 certificates, which are commonly used in SSL/TLS protocols.
Software security researchers from Loria, INRIA in France, discovered a buffer over-read vulnerability in wolfSSL library using a new protocol fuzzer called tlspuffin. CVE-2022-42905 describes this vulnerability for this critical library. WolfSSL, formerly known as CyaSSL, is a lightweight, portable, open-source implementation of Secure Sockets Layer (SSL) and Transport Layer Security (TLS) protocols. It is designed with embedded systems and resource-constrained environments in mind, offering a minimal footprint, which is highly desirable in such environments.

One important aspect of wolfSSL is its focus on strong security, with comprehensive testing and peer review to ensure robustness. Additionally, it offers support for hardware crypto and hardware acceleration to speed up operations in systems that include specific hardware for this purpose.
In terms of its use, wolfSSL can be found in a wide range of applications, including IoT devices, routers, printers, and even aviation systems, making it an important tool in the development of secure software systems.
Devastating Examples of Software Supply Chain Failures
Perhaps no incident underscores the dire consequences of supply chain failures better than the SolarWinds Orion hack. In 2020, threat actors manipulated the development process of the Orion software platform, embedding malicious code within the software updates. The widespread use of SolarWinds Orion software meant that the vulnerability reached deep into many organizations, including governmental agencies.
The direct impact of the hack was substantial. It affected as many as 18,000 SolarWinds customers, including multiple U.S. government departments and Fortune 500 companies. The data breach compromised sensitive information, potentially leading to national security threats and significant financial losses. Further, the cost of remediation, which includes identifying and removing the threat, investigating the full scope of the breach, and reinforcing security measures, was monumental.
Beyond the direct impact, the SolarWinds Orion hack also had far-reaching indirect consequences. It heightened the awareness about the potential vulnerabilities in software supply chains, leading to increased scrutiny and regulatory attention to the software development lifecycle and cybersecurity practices. It prompted organizations worldwide to reevaluate their cybersecurity strategies, particularly in relation to third-party software and supply chain risks. The hack underscored the critical importance of stringent cybersecurity measures, continuous monitoring, and rapid response capabilities in maintaining the security and integrity of digital systems.
Lastly, the SolarWinds Orion hack had a significant impact on trust — trust in software providers, in digital systems, and even in fundamental internet infrastructure. Rebuilding this trust is a complex task, requiring increased transparency, improved security practices, and, potentially, more stringent regulation and oversight. The hack served as a stark reminder that in our interconnected digital world, the security of individual components impacts the security of the entire ecosystem.
SSDLC in IoT and OT: Manufacturing, Automotive, and Healthcare
The implications of the SSDLC principles extend beyond traditional software and into the burgeoning fields of IoT and OT. With these technologies, software flaws can translate into real-world safety and security threats. In the manufacturing sector, vulnerabilities can disrupt production lines, leading to costly downtimes. In the automotive industry, breaches can compromise vehicle performance and passenger safety. Meanwhile, in healthcare, system failures and data breaches could risk patient lives and privacy. A robust SSDLC that incorporates rigorous testing and security measures is essential to mitigate these risks.
Let’s explore a following example. Rockwell Automation’s PanelView is a series of Human Machine Interface (HMI) devices used in industrial control systems. These devices provide a graphical interface that allows operators to interact with the control system of a machine or a process. The PanelView terminals are used for applications like monitoring, controlling, and displaying information graphically, enabling operators to understand the state of the operation and make informed decisions based on the presented data.
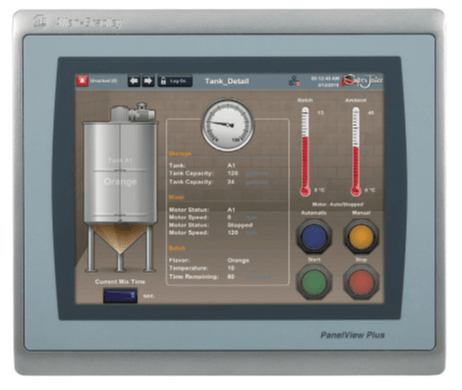
PanelView terminals come in different forms, sizes, and complexities, ranging from basic push-button models to full-featured models with touchscreens. They are used in various industrial environments including manufacturing, packaging, and process industries.
The capabilities of these devices can vary greatly, but in general, they allow users to:
1. Monitor machine or process status and performance in real-time.
2. Control operations such as starting or stopping a process, adjusting settings, or manual overrides.
3. Display and analyze historical data for performance tracking or troubleshooting.
4. Alert operators of potential issues or malfunctions through alarms or messages.
Rockwell Automation’s PanelView HMI devices can be employed in various healthcare settings to enhance efficiency, maintain quality control, and facilitate reliable operations. Some of the use cases in the healthcare industry include:
Pharmaceutical Manufacturing: In pharmaceutical production processes, PanelView can help monitor and control the manufacturing processes. This could include overseeing aspects like the mixing of ingredients, temperature and pressure control, or sterilization processes. It can also aid in ensuring stringent regulatory compliance by maintaining meticulous real-time records of process parameters and quality control data.
Medical Equipment Operations: PanelView interfaces can be integrated into various medical equipment such as dialysis machines, ventilation systems, or automated laboratory analyzers. They enable healthcare professionals to control the equipment, monitor patient status, and adjust parameters as needed.
Hospital Infrastructure Management: Hospitals often rely on complex systems for heating, ventilation, and air conditioning (HVAC), lighting, and security. PanelView can provide an interface for managing these systems, making it easier to monitor and adjust as necessary for optimal operation and energy efficiency.
Biotech and Life Sciences: In biotech and life sciences laboratories, PanelView can help manage and monitor processes such as DNA sequencing, protein synthesis, or automated cell culture systems. It can help ensure the correct conditions are maintained and alert operators to any anomalies that might compromise the validity of experiments or production.
Medical Supply Chain and Inventory Management: Automated storage and retrieval systems in healthcare can use PanelView interfaces to manage and monitor operations. This includes tracking inventory levels, automating the retrieval process, and overseeing maintenance tasks.
In these ways and more, Rockwell Automation’s PanelView helps streamline processes, maintain quality standards, and ensure reliable and efficient operations in the healthcare industry. As digital transformation continues to reshape healthcare, such tools are likely to become increasingly vital.
These devices form an essential part of the operational technology in many industrial environments, bridging the gap between humans and the automated processes. In the context of an increasingly digital industrial world, they contribute to the effectiveness and efficiency of operations, helping companies achieve higher productivity and reduced downtime.
On 11 May 2023, the US Cybersecurity and Infrastructure Security Agency (CISA), published an advisory on vulnerabilities affecting Rockwell Automation PanelView 800 that could allow remote code execution. CVSS v3 score of 9.8 is attributed to this advisory. The product is vulnerable to an out-of-bounds write, which could allow an attacker to accomplish a heap buffer overflow if the user has the email feature enabled in the project file WolfSSL uses. That feature is disabled by default. For users that require the feature, a patch is available. CISA recommends following defensive measures:
- Minimize network exposure for all control system devices, and ensure they are not accessible from the Internet.
- Locate control system networks and remote devices behind firewalls and isolate them from business networks.
- When remote access is required, use virtual private networks (VPNs), recognizing VPNs may have vulnerabilities and should be updated to the most current version available. A VPN is only as secure as its connected devices.
Regulatory Frameworks Mandating SSDLC Controls
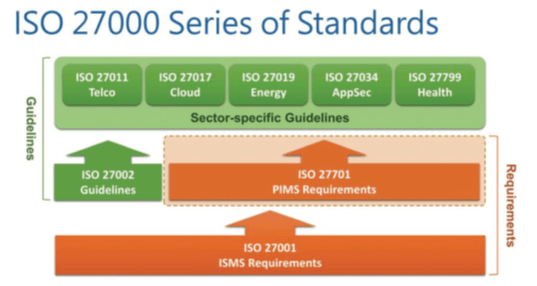
As the risk landscape evolves, regulatory frameworks are emerging that prescribe mandatory controls in SSDLC. These include standards such as ISO/IEC 27034, which provides guidelines for application security, and the NIST Cybersecurity Framework, which offers a risk-based approach to managing cybersecurity risk. These frameworks aim to ensure that organizations across industries build security into their software development processes.
In the US, building on presidential executive order on Improving the Nation’s Cybersecurity, the Office of Management and Budget issued guidance to ensure Federal agencies utilize software that has been built following common security practices. The aim is to use only software that follows secure software development standards, creates a self-attestation form for software producers and agencies, and allows the federal government to quickly identify security gaps when new vulnerabilities are discovered.
Conclusion
The Heartbleed vulnerability in OpenSSL laid bare the risks inherent in the software supply chain. Ten years later, we continue to grapple with these challenges, as demonstrated by incidents like the SolarWinds Orion hack. As the boundaries between the digital and physical world continue to blur, and as we increasingly rely on IoT and OT across industries, the need for a robust SSDLC becomes more urgent than ever. Adherence to regulatory frameworks that mandate SSDLC controls is not merely a compliance issue; it’s a necessity for the security and resilience of our interconnected world. As we look to the future, the principle is clear: security cannot be an afterthought; it must be embedded at every stage of the software development life cycle.
The article is published in Cybersecurity Trends journal No. 2 2023
I will give a keynote on this topic at CISO 360 Asia in September, organized by Pulse Conferences.